NIST SP 800-30, 800-37, 800-39, and 800-53A
How These NIST Frameworks Interconnect
In today’s rapidly evolving cyber threat landscape, organizations face an uphill battle against AI-driven attacks, supply chain vulnerabilities, and increasing regulatory pressures.
Without a structured risk management strategy, businesses risk inconsistent security assessments, poor risk prioritization, and costly compliance failures. To combat these challenges, the National Institute of Standards and Technology (NIST) provides a comprehensive suite of risk management frameworks that, when used together, form a robust cybersecurity foundation.
NIST SP 800-39, SP 800-30, SP 800-37, and SP 800-53A guide organizations in identifying, assessing, mitigating, and continuously monitoring cyber risks.
This blog explores how these frameworks interconnect, ensuring a dynamic and resilient approach to risk management.
By leveraging these frameworks as an integrated system, organizations can strengthen their cybersecurity posture, maintain regulatory compliance, and proactively manage emerging threats. Let’s dive in.
How These NIST Frameworks Interconnect: A Unified Risk Management Approach
Cybersecurity risk management isn’t a one-and-done effort—it’s an ongoing cycle of assessment, implementation, and validation.
The NIST risk management strategy is built on a continuous process that ensures cybersecurity risks are not only identified but also assessed, mitigated, and monitored dynamically.
This structured approach is guided by four interdependent publications:
NIST SP 800-39: Establishes enterprise-wide risk governance and integrates cybersecurity into business strategy.
NIST SP 800-30: Provides a structured methodology for identifying and analyzing cybersecurity risks.
NIST SP 800-37: Defines the Risk Management Framework (RMF), which applies risk assessment results to security control implementation and monitoring.
NIST SP 800-53A: Ensures security controls are effectively implemented and operating as intended.
Each of these frameworks plays a distinct role, but together they create a structured, repeatable, and scalable approach to cybersecurity risk management.
1. NIST SP 800-39: Establishing Enterprise-Wide Risk Management
Role in Risk Management
NIST Special Publication 800-39 (SP 800-39) provides a strategic framework for managing cybersecurity risks at the enterprise level. It ensures that organizations proactively integrate cybersecurity into business decision-making, rather than treating security as a standalone IT issue.
This framework helps organizations:
✔ Develop a risk-aware culture across all departments.
✔ Establish governance structures to define cybersecurity roles and responsibilities.
✔ Align security risk management with business goals and regulatory requirements.
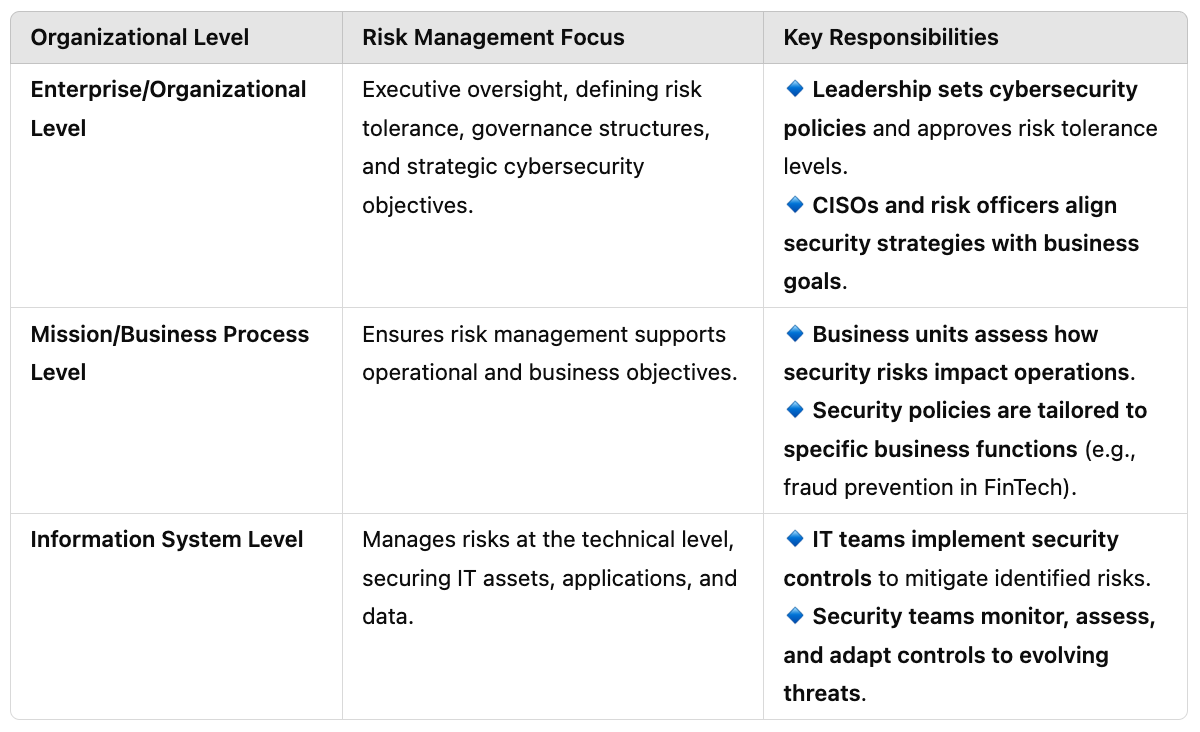
Three Organizational Levels of Risk Management
To ensure cybersecurity is holistically managed, NIST SP 800-39 structures risk management into three interconnected levels:
By structuring risk management this way, cybersecurity decisions at the executive level translate into actionable security controls at the IT level, ensuring a consistent, enterprise-wide approach to risk management.
Connection to Other NIST Frameworks
🔗 Guides Risk Assessments (SP 800-30)
Defines risk categories and impact thresholds, which serve as a foundation for structured risk assessments under SP 800-30.
Example: If an organization defines "high-risk" financial transactions as those exceeding $10 million, SP 800-30 will assess risks associated with those transactions.
🔗 Informs the Risk Management Framework (SP 800-37)
Establishes security control implementation priorities that drive the selection, deployment, and monitoring of security controls under SP 800-37.
Example: If data integrity is a top business priority, the RMF process will prioritize security controls such as encryption (SC-12) and integrity monitoring (SI-7) from SP 800-53.
🔗 Supports Control Validation and Continuous Monitoring (SP 800-53A)
Provides risk governance guidance to ensure that security controls are continuously assessed and refined using SP 800-53A methodologies.
By integrating these frameworks, NIST SP 800-39 ensures that cybersecurity is not reactive but proactively managed at all levels of an organization.
Real-World Application of NIST SP 800-39
Example: Financial Services Company Implementing NIST SP 800-39
A large financial services organization that processes high-value digital transactions applies NIST SP 800-39 as follows:
✅ Organizational Level – The CISO and board of directors define a risk tolerance policy, categorizing unauthorized access to financial data as a high-impact event.
✅ Mission/Business Process Level – The fraud prevention team tailors security policies to prevent unauthorized transactions, integrating security into business operations.
✅ Information System Level – The IT security team implements security controls, such as multi-factor authentication (MFA), encryption, and real-time fraud detection to enforce business policies.
By following SP 800-39’s approach, the organization ensures that business risk priorities guide IT security decisions, creating a structured, enterprise-wide cybersecurity strategy.
Why NIST SP 800-39 is Critical
NIST SP 800-39 provides organizations with a strategic roadmap for aligning cybersecurity with business objectives.
Without a structured enterprise-wide risk management approach, organizations may face:
❌ Fragmented security policies that do not align with business goals.
❌ Inconsistent risk assessments, leading to missed security threats.
❌ Regulatory non-compliance, resulting in fines and reputational damage.
By integrating SP 800-39 with other NIST frameworks (SP 800-30, SP 800-37, SP 800-53A), organizations can:
✅ Build a proactive cybersecurity governance model that scales with evolving threats.
✅ Ensure risk management is data-driven and business-aligned.
✅ Continuously assess and improve security controls, staying ahead of cyber risks.
Ultimately, SP 800-39 ensures that cybersecurity risk management is not just an IT issue but a business imperative.
2. NIST SP 800-30: Conducting Risk Assessments
Role in Risk Management
NIST Special Publication 800-30 (SP 800-30) provides a structured methodology for conducting comprehensive risk assessments of cybersecurity threats, vulnerabilities, and impacts. The framework helps organizations:
✔ Identify, analyze, and prioritize risks to information systems.
✔ Assess the likelihood and impact of security incidents.
✔ Make data-driven security decisions for control selection and risk mitigation.
✔ Develop a repeatable risk assessment process that supports regulatory compliance.
SP 800-30 ensures risk assessments are systematic, objective, and actionable, aligning cybersecurity risk management with business priorities.
Key Components of Risk Assessments in NIST SP 800-30
SP 800-30 defines risk assessment as a four-step process that systematically evaluates cybersecurity threats:
By systematically answering these questions, organizations can prioritize risks and allocate security resources where they are needed most.
Connection to Other NIST Frameworks
🔗 Feeds Risk Data into the Risk Management Framework (SP 800-37)
Risk assessment findings from SP 800-30 are used in SP 800-37’s RMF process to determine:
✅ Which security controls (from SP 800-53) should be implemented.
✅ The security categorization of information systems (based on FIPS 199 and FIPS 200).
✅ How risk mitigation strategies should be prioritized.
Example: If SP 800-30 identifies a high likelihood of phishing attacks, SP 800-37 will ensure that security controls like email filtering (SC-35) and security awareness training (AT-2) are prioritized.
🔗 Guides Security Control Validation via SP 800-53A
Once security controls are implemented under SP 800-37, SP 800-53A provides methodologies to test and validate whether these controls:
✅ Are correctly implemented (e.g., encryption is enabled properly).
✅ Are operating as intended (e.g., MFA actually prevents unauthorized access).
✅ Mitigate risks as expected (e.g., endpoint detection and response reduces malware infections).
Example: If SP 800-30 identifies weak authentication risks, SP 800-53A assessments will test MFA implementations to ensure they mitigate unauthorized access threats.
🔗 Supports Continuous Monitoring Under NIST SP 800-39
Risk assessments are not a one-time effort—they must be continuously updated to reflect new cyber threats and vulnerabilities.
SP 800-39 ensures that SP 800-30 risk assessments are part of an ongoing enterprise-wide risk management process.
Example: If new AI-driven phishing techniques emerge, SP 800-39 ensures that SP 800-30 risk assessments are updated, leading to revised SP 800-37 security controls and enhanced SP 800-53A testing.
Real-World Application of NIST SP 800-30
Example: Risk Assessment in a Healthcare Organization
A large hospital network applies NIST SP 800-30 to identify and mitigate risks to electronic health records (EHRs):
✅ Threats Identified: Ransomware attacks targeting patient data.
✅ Vulnerabilities Detected: Outdated EHR software with unpatched security flaws.
✅ Impact Analysis: A successful attack could lead to:
HIPAA violations and multi-million-dollar fines.
Delayed patient care, impacting lives.
Reputational loss due to media exposure.
✅ Likelihood Determined: High probability due to:Recent ransomware attacks on hospitals.
Weak email security allowing phishing attacks.
🔹 SP 800-30 results inform SP 800-37, leading to:
Implementation of multi-layered ransomware protection.
Deployment of backup and recovery controls from SP 800-53.
🔹 SP 800-53A assessments validate controls, ensuring:
Data encryption works effectively.
Incident response teams can restore systems quickly.
By using SP 800-30 in combination with other NIST frameworks, the hospital strengthens its cybersecurity posture and proactively mitigates risks before incidents occur.
Conclusion: Why NIST SP 800-30 is Essential
SP 800-30 provides a structured, repeatable, and data-driven approach to risk assessments, ensuring:
✔ Threats and vulnerabilities are systematically identified.
✔ Security measures are aligned with real-world risks.
✔ Security control selection is based on risk prioritization.
✔ Organizations remain compliant with regulatory frameworks (e.g., HIPAA, PCI DSS, GDPR).
When integrated with SP 800-37 (RMF), SP 800-53A (security control validation), and SP 800-39 (enterprise-wide risk governance), SP 800-30 ensures that cybersecurity risk management is not reactive, but proactive.
More on this topic (A Practical Guide to Risk Assessments with NIST SP 800-30)
3. NIST SP 800-37: Implementing the Risk Management Framework (RMF)
Role in Risk Management
NIST Special Publication 800-37 (SP 800-37) defines the Risk Management Framework (RMF), which provides a structured, repeatable, and adaptive approach to managing cybersecurity risk across an organization. The RMF ensures that security risk management is integrated into the system development life cycle (SDLC), rather than being an afterthought.
The primary goals of SP 800-37 are to:
✔ Ensure risk assessments drive security decisions throughout the organization.
✔ Implement and manage security controls that align with identified risks.
✔ Enable continuous monitoring and adaptation to emerging threats.
✔ Provide a standardized framework for risk-based security compliance.
By applying the RMF process, organizations can develop a scalable, risk-informed cybersecurity strategy that aligns with regulatory requirements, business needs, and emerging cyber threats.
The 7 Phases of the Risk Management Framework (RMF)
The RMF consists of seven interdependent phases, each ensuring that risk is identified, mitigated, and continuously monitored:
By following these seven RMF phases, organizations can effectively implement, validate, and improve security controls based on real-world cyber threats.
Connection to Other NIST Frameworks
🔗 Leverages SP 800-30 Risk Assessments for Security Control Selection
SP 800-37 relies on risk data from SP 800-30 to:
✅ Identify threats and vulnerabilities before selecting security controls.
✅ Determine which security controls (from SP 800-53) are necessary based on risk exposure.
✅ Prioritize controls based on risk likelihood and impact.
Example: If SP 800-30 identifies a high risk of insider threats, RMF will prioritize access control measures such as least privilege (AC-6) and audit logging (AU-2) from SP 800-53.
🔗 Uses SP 800-53A to Validate Control Effectiveness
After security controls are implemented in RMF, SP 800-53A provides testing methodologies to ensure:
✅ Security controls function as intended.
✅ Security policies align with operational security needs.
✅ Identified weaknesses are corrected before final system authorization.
Example: If SP 800-37 mandates encryption controls, SP 800-53A will validate:
Are encryption algorithms (SC-12) correctly configured?
Are encryption keys (SC-12(2)) securely managed?
🔗 Supports Continuous Risk Management via SP 800-39
RMF ensures that risk is continuously monitored in alignment with enterprise-wide cybersecurity strategies outlined in SP 800-39.
Example: If a new zero-day vulnerability is discovered, RMF’s continuous monitoring phase (Step 7) ensures:
Risk assessments are updated in SP 800-30.
New security controls are selected in SP 800-37.
Additional security testing is conducted in SP 800-53A.
By integrating these frameworks, SP 800-37 ensures that risk management is proactive, not reactive.
Real-World Application of NIST SP 800-37
Example: RMF Implementation in a Federal Government Agency
A federal agency responsible for sensitive government data applies NIST SP 800-37 as follows:
✅ Prepare – The CISO establishes risk policies, defining the agency’s risk tolerance and compliance requirements under FISMA.
✅ Categorize – Data sensitivity levels are determined using FIPS 199, identifying high-risk classified information.
✅ Select – SP 800-53 security controls (e.g., encryption, access control, auditing) are selected based on risk assessment results from SP 800-30.
✅ Implement – Security teams deploy intrusion detection systems, endpoint protection, and strong access controls.
✅ Assess – Independent auditors conduct penetration testing, configuration reviews, and control validation using SP 800-53A methodologies.
✅ Authorize – The agency’s Authorizing Official (AO) reviews security reports and grants operational approval.
✅ Monitor – The system undergoes continuous vulnerability scanning, compliance reviews, and security updates.
By implementing the RMF process, the agency ensures that cybersecurity risks are continuously evaluated, controlled, and mitigated.
Conclusion: Why NIST SP 800-37 is Essential
NIST SP 800-37 ensures that cybersecurity risk management is an ongoing process, not a one-time checklist. By following RMF, organizations can:
✔ Develop a structured and repeatable approach to cybersecurity risk management.
✔ Select and implement security controls based on real-world risk assessments.
✔ Ensure security controls are validated and continuously monitored.
✔ Meet regulatory compliance standards (FISMA, PCI DSS, GDPR, HIPAA, etc.).
When integrated with SP 800-30, SP 800-53A, and SP 800-39, SP 800-37 ensures risk-based security is effectively implemented and maintained.
4. NIST SP 800-53A: Assessing and Validating Security Controls
Role in Risk Management
NIST Special Publication (SP) 800-53A provides a structured methodology for assessing security and privacy controls in information systems and organizations. This framework ensures that security measures are:
✔️ Correctly implemented – Controls are properly configured and functioning as intended.
✔️ Operating as designed – Security measures perform effectively under real-world conditions.
✔️ Achieving expected security outcomes – Controls mitigate risks as planned and comply with regulatory requirements.
By offering consistent assessment techniques, NIST SP 800-53A enables organizations to validate security controls through objective testing, ensuring alignment with risk management strategies and compliance mandates.
Assessment Methodology in NIST SP 800-53A
The framework outlines a three-step evaluation process for testing security controls:
1️⃣ Examine – Reviewing policies, procedures, and system documentation to confirm that security controls are in place.
2️⃣ Interview – Engaging with system administrators, security personnel, and other stakeholders to validate control implementation.
3️⃣ Test – Executing technical tests (e.g., penetration testing, vulnerability scans) to verify control effectiveness under real-world conditions.
Each assessment step is mapped to specific control families from NIST SP 800-53, ensuring a structured and repeatable validation process.
Connection to Other NIST Frameworks
🔗 Validates Security Controls Implemented via RMF (SP 800-37)
NIST SP 800-37 (Risk Management Framework) requires organizations to implement security controls based on risk assessments.
SP 800-53A tests and validates whether these selected controls function effectively.
Example: If RMF mandates multi-factor authentication (MFA), SP 800-53A tests its resilience against unauthorized access (e.g., brute-force attacks).
🔗 Informs Risk Assessments in NIST SP 800-30
If an assessment reveals weaknesses in security controls, these findings inform the next risk assessment cycle in SP 800-30.
Example: If encryption controls fail confidentiality testing, risk assessors must re-evaluate the system’s threat exposure and recommend mitigation strategies.
🔗 Ensures Continuous Monitoring under NIST SP 800-39
Security control assessments feed into the enterprise-wide risk management strategy outlined in SP 800-39.
Example: If periodic assessments detect new threats, leadership may revise risk tolerance levels or allocate additional security resources.
Real-World Application of NIST SP 800-53A
Consider a healthcare organization securing electronic health records (EHRs) in compliance with HIPAA regulations. Using SP 800-53A, the organization:
✅ Examines access control policies to ensure only authorized personnel access patient records.
✅ Interviews IT administrators to verify implementation of role-based access controls (RBAC).
✅ Tests security measures by conducting simulated attacks (e.g., phishing simulations, penetration testing) to validate resilience.
Findings from these assessments inform:
SP 800-30 risk assessments, ensuring security gaps are addressed.
SP 800-37 control adjustments, improving system protection.
SP 800-39 strategic decisions, reinforcing organization-wide security priorities.
Conclusion: Why NIST SP 800-53A Matters
NIST SP 800-53A is critical for ensuring that security controls function as intended and adapt to evolving threats. By integrating assessment results into risk management workflows, organizations can:
✔️ Identify and remediate security weaknesses before they are exploited.
✔️ Maintain compliance with regulatory frameworks (e.g., PCI DSS, HIPAA, GDPR).
✔️ Support continuous security improvements through data-driven decision-making.
Ultimately, SP 800-53A acts as the quality assurance process for an organization’s cybersecurity framework, ensuring that security controls not only exist but actively protect systems and data.
Practical Example: How a FinTech Company Implements NIST’s Risk Management Frameworks
To illustrate how these frameworks work in practice, let’s consider FinSecure, a fast-growing FinTech startup specializing in digital payment processing and fraud detection. Given its role in handling sensitive financial transactions and personally identifiable information (PII), FinSecure must implement a strong cybersecurity risk management strategy.
By integrating NIST’s risk management frameworks, FinSecure ensures a structured, proactive approach to cyber risk mitigation. Here’s how each framework plays a role:
1. NIST SP 800-39: Establishing Enterprise-Wide Risk Management
At FinSecure, executive leadership, including the CISO and risk management team, defines the company’s cyber risk governance strategy. This involves:
✅ Establishing risk tolerance levels for fraud detection and payment processing.
✅ Defining governance structures for cybersecurity decision-making.
✅ Aligning security policies with industry standards like PCI DSS and ISO 27001.
By adopting SP 800-39, FinSecure ensures cybersecurity risk management is integrated into decision-making across all levels:
2. NIST SP 800-30: Conducting Risk Assessments
With governance structures in place, FinSecure’s security team conducts structured risk assessments under SP 800-30.
This includes identifying:
🔹 Threats: AI-driven phishing attacks targeting customer credentials.
🔹 Vulnerabilities: Outdated third-party API integrations exposing transaction data.
🔹 Impact: Regulatory fines, reputational damage, and financial losses.
🔹 Likelihood: A high probability of exploit attempts due to evolving fraud tactics.
By leveraging SP 800-30, FinSecure prioritizes risks, ensuring immediate threats are mitigated while lower-risk concerns remain under continuous monitoring.
3. NIST SP 800-37: Implementing the Risk Management Framework (RMF)
To mitigate identified risks, FinSecure follows the Risk Management Framework (RMF), ensuring security controls are selected, implemented, and continuously assessed. The RMF process unfolds as follows:
1️⃣ Prepare – Establish cybersecurity policies for customer authentication and API security.
2️⃣ Categorize – Classify customer payment data as high-risk based on FIPS 199 guidelines.
3️⃣ Select – Choose security controls (from SP 800-53) such as multi-factor authentication (MFA), encryption, and anomaly detection.
4️⃣ Implement – Deploy selected security controls across cloud and mobile platforms.
5️⃣ Assess – Validate security control effectiveness using SP 800-53A methodologies.
6️⃣ Authorize – Executive leadership reviews risk reports and approves system operations.
7️⃣ Monitor – Security teams continuously track threats, conduct periodic assessments, and refine controls.
By integrating SP 800-37, FinSecure ensures a structured, repeatable, and dynamic approach to cybersecurity risk management.
4. NIST SP 800-53A: Assessing and Validating Security Controls
Once security controls are in place, FinSecure’s compliance team conducts regular control assessments using SP 800-53A.
This includes:
🔍 Testing MFA authentication strength against brute-force attacks.
🔍 Evaluating encryption mechanisms for protecting customer financial data.
🔍 Conducting penetration testing to simulate real-world cyberattacks.
Findings from these assessments are fed back into SP 800-30, ensuring risks are continuously evaluated and addressed.
Why This Unified Approach Works
By integrating NIST SP 800-39, SP 800-30, SP 800-37, and SP 800-53A, FinSecure benefits from:
✅ Strategic, organization-wide risk management aligned with business objectives.
✅ Data-driven security decisions, prioritizing threats based on structured risk assessments.
✅ A structured and repeatable security process, ensuring compliance with regulations like PCI DSS and GDPR.
✅ Proactive cyber risk management, continuously adapting to emerging threats.
By following this interconnected approach, FinSecure stays ahead of cyber threats, maintains customer trust, and ensures compliance—proving that a well-structured risk management framework is a competitive advantage in the digital finance space.
Final Thoughts: The Need for a Unified Risk Management Approach
By integrating NIST SP 800-30, 800-37, 800-39, and 800-53A, organizations can:
✅ Develop a strategic, organization-wide approach to cybersecurity risk management.
✅ Prioritize cybersecurity risks based on structured assessments.
✅ Implement and monitor security controls dynamically.
✅ Ensure compliance while strengthening security resilience.
Cyber risk management is not a one-time effort but an ongoing process requiring continuous adaptation and improvement.
References
For accuracy and compliance, the following official NIST documents provide authoritative guidance on NIST SP 800-53A and its integration with other risk management frameworks:
NIST Special Publication 800-53A (Revision 5)
Title: Assessing Security and Privacy Controls in Information Systems and Organizations
Summary: Provides methodologies for evaluating security controls, including testing, documentation review, and interviews.
Source: https://csrc.nist.gov/publications/detail/sp/800-53a/rev-5/final
NIST Special Publication 800-53 (Revision 5)
Title: Security and Privacy Controls for Federal Information Systems and Organizations
Summary: Defines the control families that SP 800-53A is designed to assess.
Source: https://csrc.nist.gov/publications/detail/sp/800-53/rev-5/final
NIST Special Publication 800-37 (Revision 2)
Title: Risk Management Framework for Information Systems and Organizations
Summary: Describes how organizations implement and assess security controls as part of the RMF.
Source: https://csrc.nist.gov/publications/detail/sp/800-37/rev-2/final
NIST Special Publication 800-30 (Revision 1)
Title: Guide for Conducting Risk Assessments
Summary: Outlines risk assessment methodologies that inform SP 800-53A testing requirements.
Source: https://csrc.nist.gov/publications/detail/sp/800-30/rev-1/final
NIST Special Publication 800-39
Title: Managing Information Security Risk: Organization, Mission, and Information System View
Summary: Provides a high-level risk governance framework that integrates SP 800-53A assessments.
Source: https://csrc.nist.gov/publications/detail/sp/800-39/final
Federal Information Processing Standards (FIPS) Publication 199
Title: Standards for Security Categorization of Federal Information and Information Systems
Summary: Provides criteria for classifying information system risks, influencing SP 800-53A assessments.
Source: https://csrc.nist.gov/publications/detail/fips/199/final
How to Use These References
If you're implementing SP 800-53A assessments, refer to SP 800-53 for a complete list of control families.
When integrating security assessments into the Risk Management Framework (RMF), use SP 800-37 for control implementation guidelines.
To align assessments with broader risk governance strategies, review SP 800-39 for enterprise-wide security integration.
Stay Ahead with GRC PROS Blog Insights
🔍 Looking for more in-depth GRC insights? Subscribe to the GRC PROS blog for expert analysis, strategic guidance, and practical resources on IT Security Governance, Risk, and Compliance.
📖 Paid subscribers gain full access to our exclusive content archive, comprehensive frameworks, and actionable insights—helping you navigate the evolving GRC landscape with confidence.