Developer-Centric Compliance: Enforcing Controls in CI/CD Pipelines
GRC Cloud Audit Series - 4
In modern SaaS organizations, development teams are shipping code faster than ever — sometimes dozens of times a day. While this speed is great for innovation, it presents a unique challenge for GRC leaders:
How do you prove that security and compliance controls are enforced in a high-velocity DevOps pipeline?
In the past, compliance lived in policies, approvals, and long documentation trails. But today, that model simply doesn’t scale. Compliance must be built into the development process, enforced automatically, and evidenced continuously.
This shift — from manual oversight to developer-centric, CI/CD-integrated compliance — is essential for companies pursuing frameworks like SOC 2, ISO 27001, and HIPAA.
In this post, we’ll break down how to embed compliance into your CI/CD pipelines, the key controls auditors expect to see, and the tools that enable evidence-driven, secure software delivery.
Why Traditional Compliance Fails in DevOps
DevOps is fast, decentralized, and automated — which is great for product velocity, but difficult for legacy GRC methods to manage.
Here’s where traditional compliance often breaks down in Dev environments:
Lack of visibility into who reviewed code or merged pull requests
No standardized process for testing and release approval
Sensitive information (e.g., API keys, credentials) accidentally committed to repos
Missing or manual audit trails of deployment activities
Separation of duties is often not enforced in fast-moving teams
When these gaps are left unaddressed, they can lead to audit findings, security vulnerabilities, and delays in certification.
✅ What CI/CD Compliance Should Look Like
An audit-ready CI/CD environment can show that code changes are controlled, reviewed, and deployed securely, with full traceability.
This means demonstrating that:
All code commits go through peer review
No secrets or credentials are committed to source code
Code is scanned for vulnerabilities before deployment
Branch protection rules are enforced
Only authorized users can deploy to production
Deployment logs are maintained and accessible
CI/CD workflows are version-controlled and monitored
And just as important — these activities are automated and evidenced.
Key CI/CD Controls Auditors Look For
🔒 1. Change Management
Are code changes tracked through version control?
Are changes peer-reviewed before merging?
Can you show a complete audit trail of who changed what, when, and why?
🛡 2. Code Review & Approval
Is there a policy for code review?
Are branch protection rules configured to require reviews and approvals?
Are reviewers restricted based on roles?
🧪 3. Pre-Deployment Testing & Validation
Are unit tests, security scans, and static code analysis (SAST) part of the pipeline?
Are builds blocked if critical issues are detected?
🤐 4. Secret Management
Are tools in place to detect hardcoded secrets in code?
Are secrets rotated and managed via secure vaults or key management systems?
🧾 5. Audit Logging & Monitoring
Can you produce logs of CI/CD pipeline runs, deployments, and user actions?
Are these logs stored securely and retained per policy?
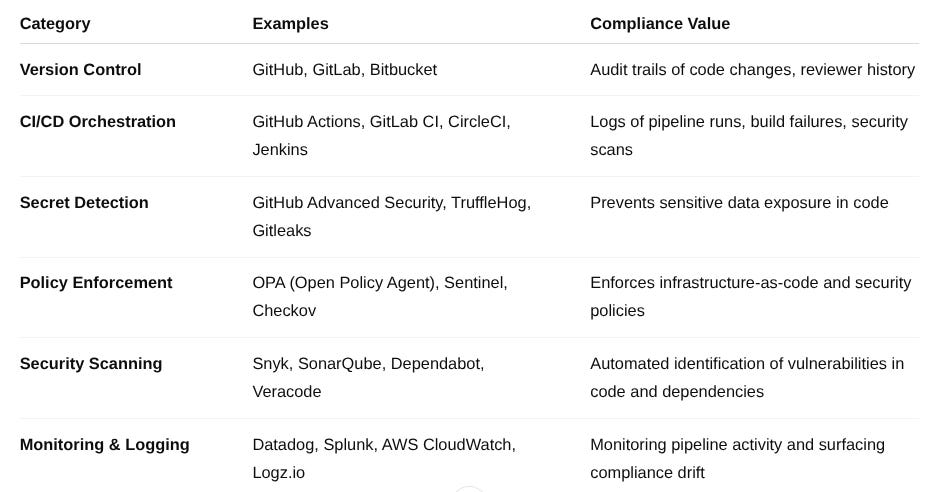
Tools That Support Compliance in CI/CD
To enforce and evidence controls, GRC and engineering teams should work together to integrate tools that support:
By combining these tools with centralized GRC platforms (like Drata, Secureframe, or Sprinto), you can pull CI/CD activity into your compliance evidence library automatically.
How to Integrate Compliance into CI/CD Workflows
Embedding compliance into your CI/CD pipelines transforms audit readiness from a once-a-year scramble into an automated, continuous capability.
Below is a structured, evidence-driven approach to building pipelines that meet auditor expectations without slowing down delivery.
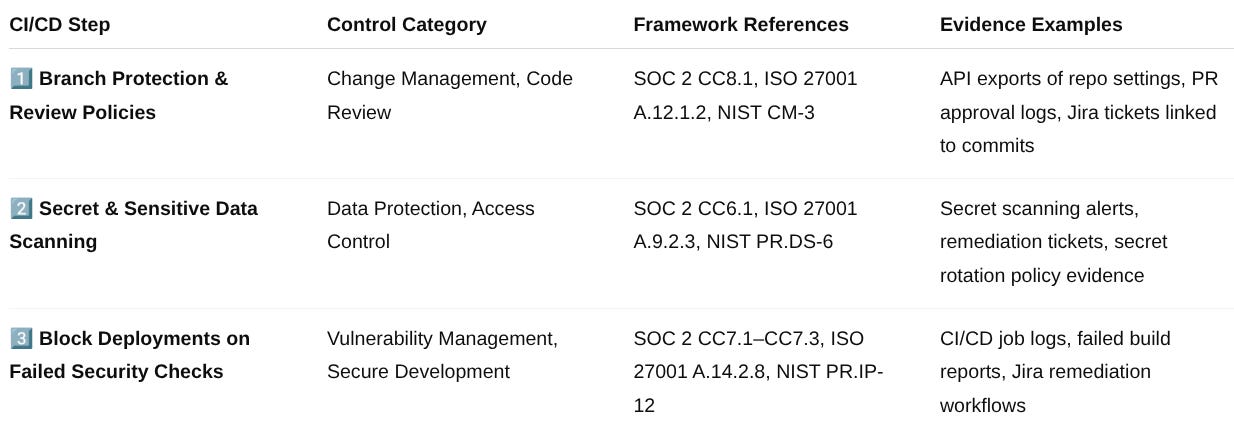
✅ 1. Enforce Branch Protection and Review Policies
Strong branch protection is the foundation of change management. It ensures all code changes are reviewed, tested, and approved before deployment.
In GitHub (or GitLab/Bitbucket):
Require pull request reviews with at least two approvers.
Dismiss stale approvals when new commits are pushed.
Require status checks (e.g., SAST scans, build tests) to pass before merges.
Restrict who can push or merge into protected branches (e.g.,
main,production).
Operational Tip:
Use GitHub’s REST or GraphQL API to export branch protection configurations as evidence rather than relying on screenshots — auditors appreciate verifiable data.
📌 Evidence Examples:
API exports of repo settings showing protection rules
Logs of PR approvals and merges
Jira tickets linked to pull requests or deployment commits
✅ 2. Scan for Secrets and Sensitive Data
Human error is inevitable — but hardcoded secrets shouldn’t make it into production.
Automated scanning must exist at multiple points in the pipeline.
Implementation:
Integrate TruffleHog, GitGuardian, or GitHub Secret Scanning as pre-commit hooks and CI jobs.
Detect API keys, credentials, or certificates before they reach main.
Enforce automatic blocking and alerting for detected secrets.
Track remediation through your issue-tracking system (e.g., Jira).
Best Practice:
Rotate any exposed keys immediately and document the incident response steps in your compliance platform.
📌 Evidence Examples:
Secret scanning logs and alerts
Jira remediation tickets
Policy or playbook references for secret rotation
✅ 3. Block Deployments on Failed Security Checks
Security cannot be optional. Automated gates within your CI/CD pipeline should stop any release that fails core security validations.
Implementation:
Use Snyk, SonarQube, or OWASP Dependency-Check for vulnerability and dependency scanning.
Set pipelines to fail automatically when high-severity vulnerabilities are detected.
Require successful completion of unit, integration, and security tests before deploy.
Advanced Control:
Use “build promotion” rules — artifacts must pass scans before moving from staging to production environments.
📌 Evidence Examples:
CI/CD job logs showing test results and failed builds
Security scan reports
Jira tickets documenting remediation and retesting
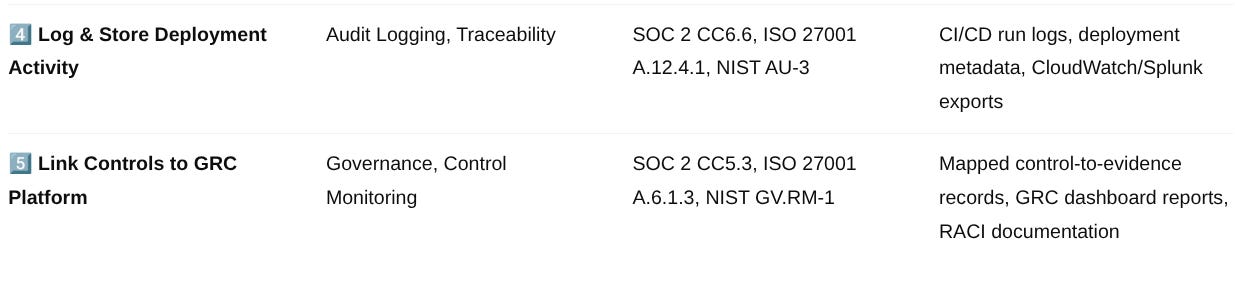
✅ 4. Log and Store Deployment Activity
Every deployment event should be auditable — who initiated it, when it occurred, what changed, and why.
Implementation:
Enable detailed logging in CI/CD tools (GitHub Actions, GitLab CI, Jenkins).
Include metadata like commit ID, environment, and build number.
Export logs to centralized systems (e.g., AWS CloudWatch, Splunk, ELK).
Retain for the period defined by your frameworks — typically 1–3 years for SOC 2 or ISO 27001.
Pro Tip:
Correlate deployment logs with change management tickets to form a continuous audit trail.
📌 Evidence Examples:
CI/CD run logs with user and commit details
Exported logs in CloudWatch or Splunk
Change request IDs linked to deployment records
✅ 5. Tie Everything Back to Controls
Automation and logs mean nothing if they’re not traceable to controls. GRC alignment closes the loop between technical enforcement and governance.
Implementation:
Map each pipeline control (e.g., “peer review required”) to specific framework clauses such as SOC 2 CC8.1, ISO 27001 A.14.2.9, or NIST PR.DS-7.
Tag all evidence artifacts by control ID and framework in your GRC platform (e.g., Drata, Secureframe, RiskConnect).
Assign control ownership to the responsible DevOps or engineering role — not just to “Security.”
Result:
Auditors can trace a direct path from framework → control → pipeline enforcement → evidence. This linkage demonstrates operational maturity and continuous control effectiveness.
📌 Evidence Examples:
GRC dashboard showing mapped CI/CD controls
Control ownership records and RACI matrices
Control pass/fail status reports or compliance exports
Bottom Line:
Compliance in CI/CD isn’t about adding bureaucracy — it’s about embedding assurance into automation.
When your pipelines are instrumented to enforce, record, and map controls automatically, you eliminate audit friction and turn compliance into a built-in business advantage.
CI/CD Compliance Integration Summary
Key Takeaway:
When every CI/CD step maps directly to a control category, framework reference, and verifiable evidence source, you eliminate ambiguity during audits and demonstrate mature, continuous compliance operations.
CISO Takeaway: Why This Matters
For CISOs and GRC leaders, embedding compliance within CI/CD pipelines isn’t just a security measure — it’s a strategic governance shift.
When controls are enforced through automation, every deployment becomes a verifiable compliance event. That means less audit fatigue, faster evidence retrieval, and stronger confidence from auditors, investors, and customers alike.
This approach transforms GRC from a reactive oversight function into a real-time governance system — one that proves your organization can scale at DevOps speed without sacrificing assurance.
Ultimately, audit readiness isn’t a goal you reach once a year — it’s a continuous state of operational trust built into your delivery pipeline.
Developer Responsibility: Turning Governance into Code
While CISOs define the governance model, developers bring it to life.
Compliance doesn’t live in policies or audit binders anymore — it lives in the codebase, in the pipeline logic, and in the automation that enforces security without slowing innovation.
When developers understand the “why” behind GRC requirements, compliance stops being an external obligation and becomes part of software craftsmanship.
Peer reviews, secret scanning, and pipeline gates aren’t red tape — they’re assurance mechanisms that protect the integrity of every release.
For DevOps and engineering teams, this shift means:
Building controls into tools they already use — GitHub, Jenkins, Jira — instead of relying on manual review cycles.
Using automation to generate evidence continuously rather than collecting screenshots during audits.
Treating compliance failures as code quality defects, not administrative issues.
When developers and security teams operate from the same workflow, compliance becomes invisible — embedded, traceable, and verifiable by design.
This is where governance and innovation converge: a state where every deployment is not just fast, but provably secure and audit-ready.
From Principle to Practice
Now that we’ve defined how governance translates into developer-led execution, let’s look at what this actually means in a real-world audit scenario.
The following example walks through a SOC 2 Type II audit of a DevSecOps pipeline, showing how automated controls, evidence collection, and developer-centric compliance come together to create a continuously audit-ready environment.
🔁 Example: SOC 2 Audit of a DevSecOps Pipeline
🔁 Example: SOC 2 Audit of a DevSecOps Pipeline
Imagine you’re preparing for a SOC 2 Type II audit covering a 12-month period. Your environment runs on AWS with GitHub Actions managing CI/CD, and your auditor wants to understand exactly how you ensure secure code deployment — from developer commit to production release.
Here’s what “audit-ready” looks like in a mature DevSecOps workflow:
GitHub Repository Settings:
The main branch is protected with required status checks and two mandatory code reviewers. Merges without review are automatically blocked, and stale approvals are dismissed if code changes after review.
→ Evidence: API exports or screenshots of branch protection rules from GitHub settings.Secret Scanning and Credential Control:
GitHub Advanced Security is configured to scan for hardcoded secrets, API keys, and credentials in every pull request. Alerts automatically create Jira tickets for remediation, and no code can merge until the issue is resolved.
→ Evidence: Secret scanning logs, Jira remediation records, and policy enforcement settings.CI/CD Pipeline Security Gates:
The CI pipeline executes static application security testing (SAST) and dependency scanning (SCA) before allowing a build to proceed. If a high-severity vulnerability is found, the build fails automatically, forcing remediation before deployment.
→ Evidence: CI job logs showing test results, failure gates, and build pass/fail history.Change Management Traceability:
Each code change links to a Jira ticket or change request, providing a full audit trail from request → approval → implementation → deployment.
→ Evidence: Jira issue history, GitHub PR metadata, and commit IDs tied to deployment records.Automated GRC Integration:
Compliance data flows into your GRC platform (e.g., Drata, Secureframe, or RiskConnect) in real-time. The platform displays your “Change Management” control as continuously passing, showing consistent enforcement of peer review, testing, and approval controls across the audit period.
→ Evidence: Drata dashboard snapshots, control audit logs, and continuous monitoring reports.Deployment Logging and Retention:
GitHub Actions logs every pipeline execution, capturing who initiated it, when, and what commit was deployed. Logs are automatically exported to AWS CloudWatch or Splunk for long-term retention, ensuring traceability for the entire audit window.
→ Evidence: Deployment logs, CloudWatch exports, and pipeline metadata.
When you present this to your auditor, you’re not showing static screenshots or point-in-time evidence — you’re demonstrating a continuous control system that automatically enforces and documents every step in the DevOps lifecycle.
This creates a seamless, verifiable chain from:
Change request → Code review → Security validation → Deployment → Audit evidence.
That’s what a truly audit-ready DevSecOps pipeline looks like — automated, traceable, and resilient by design.
In Closing
Compliance embedded in your CI/CD pipeline isn’t a “nice to have”—it’s a competitive advantage.
When every commit, every merge, every deployment is traceable, control-mapped, and evidenced, your audit teams breathe easier, your developers stay in flow, and your business proves it doesn’t just ship features—it ships them securely and sustainably.
Build this once, and every release becomes a statement of trust.
References
Nagpal, A., Pothineni, B., Parthi, A. G., Maruthavanan, D., Banarse, A. R., Veerapaneni, P. K., Sankiti, S. R., & Jayaram, V. (2024). Framework for automating compliance verification in CI/CD pipelines. International Journal of Computer Science and Information Technology Research (IJCSITR), 5(4), 17-27. ResearchGate+1
U.S. National Security Agency (NSA) & Cybersecurity and Infrastructure Security Agency (CISA). (2023). Defending Continuous Integration/Continuous Delivery (CI/CD) Environments. Cybersecurity Information (CSI) Sheet. U.S. Department of War
CircleCI. (2023). Simplifying Compliance with CI/CD. [Whitepaper] CircleCI