In today’s SaaS ecosystem, compliance is not the goal — trust is. Security frameworks like SOC 2 and ISO 27001 are only valuable when they support a larger strategy: protecting customer data, proving operational maturity, and enabling growth.
Customers, investors, partners — and increasingly, regulators — don’t just want to see a SOC 2 report or ISO 27001 certificate; they want to understand how your controls work, why they exist, and whether they actually protect their data.
That’s why leading SaaS providers are shifting their mindset:
✅ From checklist compliance to risk-driven assurance
✅ From one-time certifications to continuous, auditable security operations
✅ From vague policies to evidence-backed, outcome-focused controls
But this shift introduces a new challenge — one that many fast-growing SaaS companies struggle to navigate:
How do you build a security program that is both risk-informed and framework-aligned — one that addresses real threats and passes external audits with confidence?
The Challenge: Aligning Real-World Risk with Formal Frameworks
SOC 2 and ISO 27001 are intentionally flexible — and that flexibility is both a strength and a trap.
Flexibility allows organizations to implement controls suited to their architecture, business model, and threat landscape.
But ambiguity often leaves teams guessing whether their controls will hold up under audit scrutiny.
This creates a tension:
Focus too much on real-world risk, and you risk audit gaps due to insufficient documentation or alignment.
Focus too much on audit checklists, and you risk deploying shallow controls that don’t truly reduce exposure — leaving you certified but still vulnerable.
The SaaS companies that thrive in this space are the ones that understand how to bridge that gap.
They design risk-based controls, informed by frameworks like ISO 27005 and NIST RMF, then explicitly map those controls to SOC 2 Trust Services Criteria and ISO/IEC 27001:2022 Annex A requirements.
They don’t just do security — they prove it, with traceable, well-documented, and continuously validated controls that both satisfy auditors and strengthen the business.
📘 What This Blog Covers
In this comprehensive guide, we provide a blueprint for SaaS organizations to align risk-based security programs with the formal requirements of SOC 2 and ISO 27001.
Whether you’re preparing for your first audit or refining a mature GRC program, this article walks you through:
Establishing a Risk Management Framework – Using ISO 27005 and NIST RMF to define and evaluate risks.
Designing Risk-Based Controls – Implementing proportional and evidence-driven safeguards.
Mapping Controls to Framework Requirements – Aligning every control to specific clauses in SOC 2 and ISO/IEC 27001.
Building Control Evidence for Audit and Operations – Creating repeatable, reliable proof of control effectiveness.
Operationalizing Framework Maintenance – Moving from annual audits to continuous governance cycles.
Designing Policies That Reflect Risk and Compliance – Building policy documents that anchor your program in both standards and reality.
Focusing on Common Control Areas – A deep dive into high-priority domains like access control, change management, and vendor risk.
Who This Is For
This guide is tailored to:
CISOs, Heads of Security, and Compliance Leads building risk-aligned security programs
GRC Managers and Consultants preparing for SOC 2 or ISO 27001 implementation
Engineering Leaders responsible for enabling security controls without slowing down innovation
SaaS Founders and Executives seeking to scale trust alongside product growth
Whether you’re building from scratch or optimizing an existing compliance program, this guide will help you align your operational security with business risk and framework expectations — creating a security posture that is credible, scalable, and resilient.
Let’s dive in — starting with the foundation of any strong GRC program: a well-defined, risk-driven approach to security.
SOC 2 vs. ISO/IEC 27001 Comparison Overview
Use this brief comparison to help readers understand context at a glance:
SOC 2
Focus: Trust Services Criteria (Security, Availability, Confidentiality, etc.)
Region: U.S.-centric
Audit Type: CPA attestation (Type 1 or Type 2)
Control Prescriptiveness: Low – flexible and principle-based
Best for: U.S. B2B SaaS companies selling to regulated customers
ISO/IEC 27001:2022
Focus: Information Security Management System (ISMS)
Region: Global, especially Europe, APAC, and regulated industries
Audit Type: Certification from an accredited body
Control Prescriptiveness: Medium – control catalog via Annex A
Best for: SaaS companies needing international trust or formal security governance
Step-by-Step Guide to Aligning Risk-Based Security with SOC 2 & ISO 27001
Step 1: Establish a Risk Management Framework (ISO 27005 or NIST RMF)
Before implementing any security controls — and long before audit season — your SaaS organization must embed risk management into the DNA of your security program.
Frameworks like ISO/IEC 27005 and the NIST Risk Management Framework (RMF) provide structured, proven approaches to doing just that.
Why This Step Matters
SOC 2 and ISO 27001 aren’t just lists of controls — they require contextual security, where every control is traceable to a business risk.
Auditors and stakeholders want to see that your security is not arbitrary, but grounded in a systematic and repeatable risk process.
Key Building Blocks of a Mature Risk Management Framework
Let’s walk through each foundational step in detail:
1. Identify and Categorize Information Assets
Before you can protect anything, you need to make a full list of what you’re protecting.
In security terms, these are your information assets—the systems, tools, and data that keep your SaaS business running.
Think of it like making a home inventory for insurance: you write down what you own, where it is, and how valuable it is. The same idea applies to SaaS security.
What Counts as an “Information Asset”?
For a SaaS company, your assets include:
Product environments: Your main software product and its different versions (production, staging, development).
Cloud infrastructure: The servers and storage you rent from providers like AWS, Azure, or GCP.
Databases & storage: Where your customer data lives—like AWS S3 buckets, RDS, or BigQuery.
Source code: The code that powers your SaaS, stored in places like GitHub or GitLab.
Internal tools: Business apps your team uses, such as Jira, Slack, or Notion.
APIs & integrations: The connections between your product and other services.
Third-party vendors: Any outside companies you rely on to process or store data.
Customer data sets & PII: The actual sensitive data (names, emails, payment info, health info, etc.) your SaaS is trusted to protect.
Why This Step Matters
If you don’t know exactly what you have, you can’t:
Assess which systems are most sensitive.
Spot risks that matter most.
Prove to auditors that you’re systematically managing security.
How to Make It Practical
When listing assets, tag each one with:
Ownership – Who’s responsible for it? (e.g., DevOps lead, IT manager).
Sensitivity – How sensitive is the data? (e.g., confidential, public).
Criticality – How important is it to the business? (e.g., business-critical, backup only).
This gives you a clear picture of what matters most so you can prioritize protections and investments.
Why Frameworks Care
ISO 27005 calls this “asset identification and valuation” because you’re not just listing assets—you’re also judging their importance.
NIST RMF Step 1 calls it “categorizing information systems,” which is basically the same idea: know what you have, know how important it is, and label it accordingly.
👉 In plain terms: You can’t lock the doors if you don’t know how many doors your house has, or which ones lead to the valuables.
2. Identify Threats and Vulnerabilities
Once you’ve made a list of your important systems and data (your assets), the next step is figuring out what could go wrong with them.
This is where you identify threats and vulnerabilities.
Threats are bad things that could happen to your assets. Think of them as potential “attacks” or “scenarios.”
Examples: Someone stealing login credentials, a hacker exploiting a bug, or an employee falling for a phishing email.Vulnerabilities are weak spots in your systems that make it easier for threats to succeed.
Examples: Software that hasn’t been updated, overly broad user permissions, or a cloud storage bucket left publicly accessible.
You don’t have to come up with these entirely on your own. Companies usually use a mix of:
Internal knowledge: Your own IT, DevOps, and compliance teams know where the business may have weaknesses.
External resources: Industry guides like OWASP Top 10 (common web risks), MITRE ATT&CK (attack techniques), or threat intelligence feeds that track real-world attacks.
Example in SaaS terms
Imagine your company stores customer data in AWS S3 buckets (a type of cloud storage).
Threat: A malicious actor could gain access and expose that customer data to the public.
Vulnerability: The bucket is misconfigured (for example, marked as “public” when it shouldn’t be).
The result? Sensitive customer data could leak, causing compliance failures and reputational damage.
Why Frameworks Care
ISO 27005 calls this step “threat and vulnerability identification.” It’s about making sure you’re not protecting blindly—you know exactly what risks exist.
NIST RMF Step 2 says “select and analyze threats.” This ensures you analyze risks methodically instead of guessing.
👉 In simple terms: Think of it like locking your house. First you list what’s inside worth protecting (your assets). Then you check what could go wrong (threats—like a burglar or fire) and where your defenses are weak (vulnerabilities—like an unlocked window or faulty smoke detector).
3. Assess Likelihood and Impact
After you’ve listed your risks (Step 2), the next question is: Which ones are the biggest deal?
To figure that out, you score each risk based on two factors:
Likelihood – How likely is it to happen? (once a year vs. once in a decade)
Impact – If it does happen, how bad would it be? (minor inconvenience vs. major financial and reputational damage)
Ways to Measure Risks
You can keep it simple or get very detailed, depending on your organization’s maturity:
Qualitative (Simple) – Use labels like High / Medium / Low.
Example: “A phishing attack is High likelihood, Medium impact.”Quantitative (Detailed) – Put numbers on it.
Example: “If this happens once a year, it could cost $200,000 in damages.”Hybrid – Combine both approaches using models like FAIR (Factor Analysis of Information Risk), which blends numbers and categories.
Tools to Visualize Risk
Most organizations use a risk matrix (a grid showing likelihood vs. impact) or a heat map (color-coded chart) to visualize where the biggest risks are.
Top right corner = high likelihood and high impact → deal with it immediately.
Bottom left = low likelihood and low impact → may not be worth heavy investment.
Why This Step Matters
Business value: Helps leadership understand which risks deserve attention and resources.
Compliance value: Auditors want proof that risks are not just listed, but evaluated in a structured way.
Why Frameworks Care
ISO 27005 calls this “risk analysis and evaluation.” It’s about making sure you don’t treat all risks the same.
NIST RMF Step 3 says “assess risks,” which is basically the same: understand how likely they are and how much damage they’d cause.
Key Reminder
Not every risk requires immediate action. Some risks can be:
Accepted (you live with them), or
Transferred (you shift them to someone else, like an insurance company).
But whatever you decide, it must be documented and justified in your risk register.
👉 In plain terms: Think of this like managing household safety. If your house has a leaky roof (big risk), you fix it right away (mitigate). If you live in a flood zone, you might buy flood insurance (transfer). If you have a dangerous balcony you never use, you might block it off completely (avoid). And if your fence has a tiny crack, you might just accept it and check back later.
4. Prioritize Risks and Define Risk Treatment Plans
By now, you’ve already:
Listed your assets (Step 1).
Identified threats and vulnerabilities (Step 2).
Scored each risk for likelihood and impact (Step 3).
Now comes the practical part: deciding what to do about those risks.
Why Prioritization Matters
Not all risks are equal. Some could take down your business if they happen, while others might just cause small annoyances.
Because you don’t have unlimited time, money, or people, you need to focus first on the risks that matter most.
This prioritization guides:
Which security controls to roll out first (e.g., MFA before minor logging tweaks).
Where to spend budget or engineering time (e.g., protecting customer data storage before upgrading low-risk tools).
How to link your actions back to compliance (SOC 2 and ISO 27001 require you to document your treatment choices).
The Four Risk Treatment Options
Once you know which risks are unacceptable, you decide how to handle them:
Mitigate – Put in controls to reduce the risk.
Example: Enable multi-factor authentication (MFA) to reduce the chance of stolen credentials being used.Transfer – Shift the risk to someone else.
Example: Buy cyber insurance or require a vendor to assume responsibility in a contract.Avoid – Change your processes so the risk goes away entirely.
Example: Stop storing sensitive data you don’t really need, so there’s nothing to steal.Accept – Acknowledge the risk and keep an eye on it.
Example: You may decide that a very low-likelihood risk isn’t worth fixing right now, but you’ll monitor it.
What Makes This Step “Audit-Ready”
Every risk decision must be:
Documented: Recorded in the risk register with clear justification.
Approved by management: Risk acceptance or treatment decisions must be owned at the leadership level, not left solely to IT.
Framework-mapped: Each treatment must be explicitly linked to SOC 2 Trust Services Criteria or ISO 27001 Annex A controls, so auditors can trace risk → decision → control.
Why Frameworks Care
ISO 27005 calls this “risk treatment selection and implementation.” It’s about proving you have a formal, consistent process for deciding what to do with risks.
NIST RMF Step 4 is “Respond to Risk.” It emphasizes that every risk must lead to a conscious, documented decision.
👉 In plain terms: Think of this like managing household safety. If your house has a leaky roof (big risk), you fix it right away (mitigate). If you live in a flood zone, you might buy flood insurance (transfer). If you have a dangerous balcony you never use, you might block it off completely (avoid). And if your fence has a tiny crack, you might just accept it and check back later.
5. Establish Ongoing Risk Monitoring
Security isn’t something you set up once and walk away from. New risks pop up all the time:
Your company launches new features.
Hackers find fresh attack methods.
Employees adopt new tools or vendors.
That means your risk program is never “finished.” To stay secure, you need to continuously monitor your risks and update your safeguards as things change.
What Ongoing Monitoring Looks Like
Instead of waiting for the yearly audit, SaaS companies should build a repeatable cycle of reviews and checks:
Quarterly Risk Reviews: Every few months, go back to your risk register (your master list of risks) and check if they’re still accurate.
Annual Risk Re-Assessments: Once a year, take a deeper look—are new threats emerging? Are old risks no longer relevant?
Risk Indicators and Metrics (KRIs): Track signals that show when risk is increasing. For example: number of failed logins, number of unpatched systems, or vendor security ratings.
Integration with Security Activities: Feed insights from vulnerability scans, penetration tests, and incident reports into your risk program so it reflects reality, not just theory.
Why This Step Matters
For the business: It helps you catch small issues before they grow into big problems.
For auditors: It proves you’re not just doing “point-in-time” compliance—you’re managing risks throughout the year.
For customers: It builds confidence that your SaaS security is proactive, not reactive.
Why Frameworks Care
ISO 27005 calls this “risk monitoring and review.” The goal is to show that risk assessments are living documents, not one-off tasks.
NIST RMF Step 5 is “Monitor Security Controls.” It emphasizes that controls must keep working effectively over time, not just on day one.
Bonus Tip
If you use a GRC platform (like LogicGate, Vanta, or Drata), you can tie your risk register directly into these tools. That way, when something changes—like a new asset is added, or a scan finds a vulnerability—the system automatically flags it. This reduces manual effort and keeps your monitoring process consistent.
👉 In simple terms: Think of security like maintaining a car. You don’t just buy it and hope it runs forever—you check the oil, rotate the tires, and get regular inspections to make sure it’s still safe on the road.
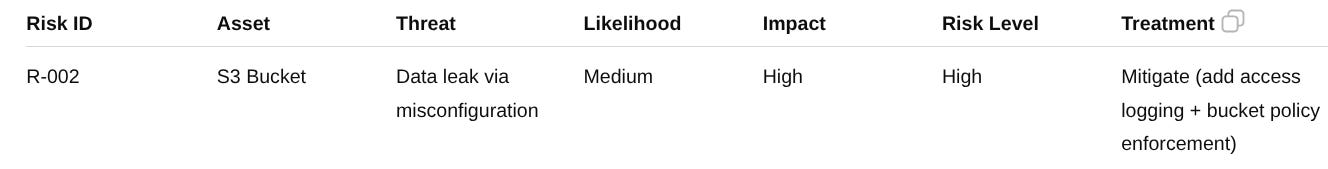
📋 Example: Risk Register Entry
Step 2: Map Risk-Based Controls to SOC 2 Trust Services Criteria (TSC) and ISO 27001 Annex A
Implementing risk-based controls is a strong start — but for those controls to satisfy compliance frameworks like SOC 2 and ISO 27001, they must be formally mapped and justified within the context of each standard.
This step bridges the gap between “doing security” and proving security through structured control alignment.
Why Mapping Controls Matters
SOC 2 and ISO 27001 are outcome-based frameworks. They don’t tell you exactly how to implement security — they define objectives and expect your implementation to meet the intent.
Auditors expect to see a clear chain of traceability:
The risk identified
The control implemented to address it
The framework requirement that the control fulfills
Without this linkage, even strong controls may be flagged as insufficient.
Mapping ensures you’re not over-engineering controls or missing critical coverage areas.
How to Map Controls to Framework Requirements
Mapping controls to compliance framework requirements is a foundational skill in any mature GRC program.
Whether you’re aligning your security program with SOC 2 Trust Services Criteria (TSC) or ISO/IEC 27001:2022 Annex A, the ability to clearly demonstrate how your implemented controls meet compliance expectations is key to achieving certification, passing audits, and managing risk effectively.
Below, we walk through a practical, step-by-step approach to mapping controls to framework requirements — starting with the risk register and ending with traceability across multiple frameworks.
1: Start with Your Risk Register
The foundation of any control mapping exercise is a well-structured risk register.
Before mapping any controls, you should already have:
Identified relevant business and technical risks
Assessed likelihood and impact
Chosen a treatment strategy: mitigate, accept, transfer, or avoid
Assigned risk owners and mitigation timelines
Example Risk Entry:
At this point, this risk needs to be treated with controls that both reduce the risk and align with the compliance frameworks your organization is targeting.
2: Implement Risk-Based Controls
Controls should be proportional, operationally feasible, and evidenced. When choosing controls, consider:
The nature and criticality of the risk
Your operating model (e.g., SaaS, hybrid cloud, on-premise)
The resources available for implementation and monitoring
Auditability: Can you demonstrate that the control is effective?
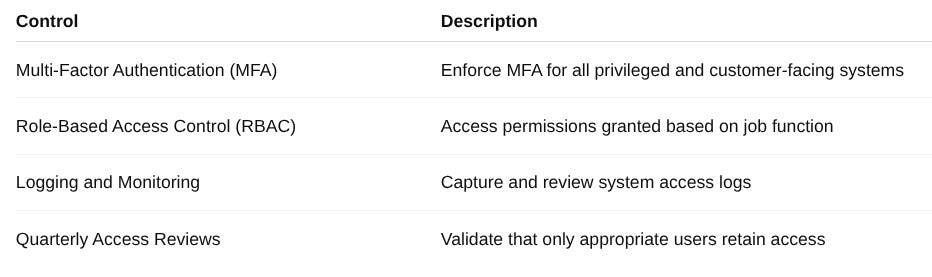
Selected Controls for Risk R-001 (Unauthorized Access):
These controls are directly aimed at reducing the risk of unauthorized access and can be mapped to framework requirements in both SOC 2 and ISO/IEC 27001:2022.
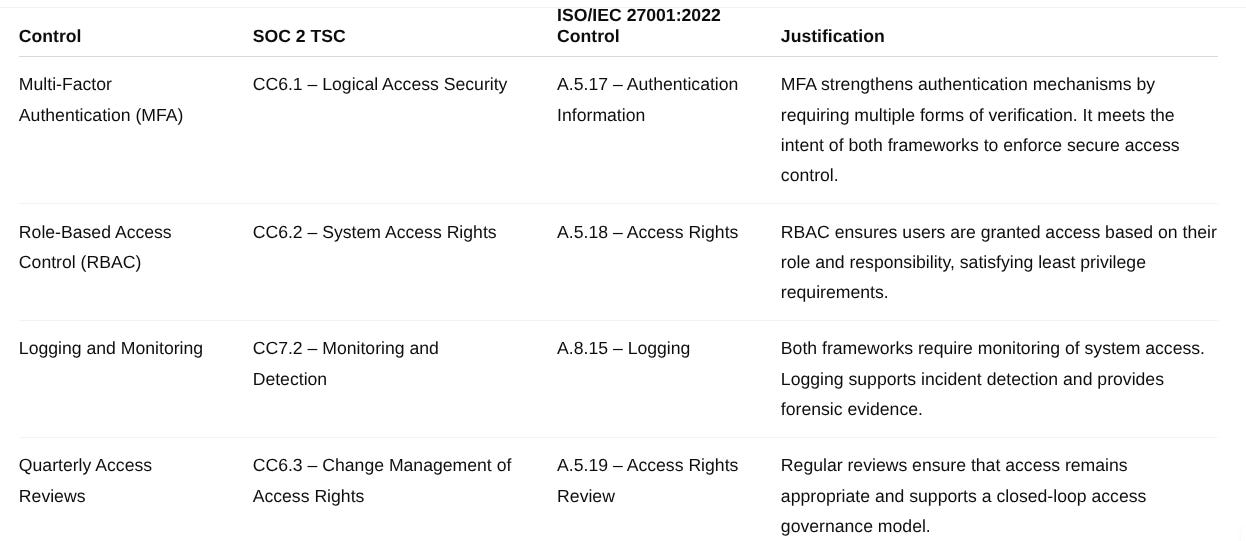
3: Map Each Control to Framework Requirements
To demonstrate compliance, we now map each selected control to both SOC 2 TSC and ISO/IEC 27001:2022 Annex A controls.
The objective is to show how the control:
Addresses a specific risk
Fulfills the intent of the framework requirement
Is supported by evidence
4: Document the Mapping in a Traceability Matrix
A Control-to-Requirement Mapping Matrix is a powerful tool that allows you to show one-to-many relationships:
This matrix helps you demonstrate to auditors and internal stakeholders that:
You have controls in place that treat real, documented risks
Those controls are linked directly to industry-standard frameworks
You can show evidence of control design, operation, and effectiveness
💼 Why This Matters
Mapping controls to frameworks is not just a compliance exercise — it provides:
✅ Clarity on how your security investments reduce real risk
✅ Confidence during audits and certification assessments
✅ Consistency across overlapping framework requirements
✅ Efficiency, avoiding duplication by using one control to meet many requirements
Instead of building your GRC program around checklist compliance, this approach anchors everything to risk-based decision-making.
5. Define Control Ownership and Accountability
Every control should have a named owner — not a team, but a person responsible for:
Ensuring the control is operating effectively
Updating evidence and documentation
Participating in audits and assessments
Reviewing control metrics and KPIs
✅ Pro Tip: Use GRC platforms like Drata, Vanta, Tugboat Logic, or custom Jira dashboards to assign and track control ownership automatically.
6. Tie Controls to Policies and Procedures
Auditors expect to see that your control implementation is backed by formal documentation.
This includes:
Policy: Describes the rule (e.g., “All production access requires MFA.”)
Standard/Procedure: Describes how the rule is implemented (e.g., “All AWS IAM users must have MFA enabled. SOC team reviews logs weekly.”)
Records/Evidence: Shows the rule is followed (e.g., MFA configuration logs, access review records)
Make sure your Control Matrix references these documents clearly.
Outcome: Controls That Are Meaningful, Auditable, and Aligned
By mapping your risk-based controls to SOC 2 and ISO 27001:
You demonstrate control intentionality (you’re not just copying a checklist)
You accelerate audit readiness by showing traceability from risk → control → requirement → evidence
You create a living control environment that can evolve with your business, threat landscape, and compliance needs
Step 3: Build Control Evidence That Serves Both Audit and Security Needs
Implementing security controls is one thing. Proving that they work — consistently, reliably, and as designed — is what makes the difference between passing an audit and failing one.
Auditors aren’t only checking whether a control exists — they want assurance that it operates consistently and reliably over time. To satisfy SOC 2 and ISO 27001, evidence must demonstrate that:
Consistency: The control is applied the same way every time, not just occasionally.
Effectiveness: The control actually reduces the specific risk it was designed to address.
Traceability: The control links back to documented policies, procedures, and framework requirements, supported by reliable evidence.
Equally important, your security team needs this same evidence for internal monitoring, incident response, and continuous improvement.
That’s why building dual-purpose evidence — useful for both audits and security operations — is a key SaaS best practice.
🧱 What Makes Good Control Evidence?
Strong evidence has 3 qualities:
Objective: Factual records (e.g., logs, screenshots, configs), not just verbal assurances.
Repeatable: Can be reproduced on demand, across different time periods, showing the control is consistently enforced.
Relevant: Directly proves that the control is meeting the risk-reduction objective it was designed for.
⚖️ Remember: Weak evidence (like undocumented practices or one-off screenshots) may get flagged by auditors as unreliable or insufficient.
📂 Types of Control Evidence
Here’s a breakdown of the core categories of evidence you should capture:
1. Policy Documents
High-level rules that set the expectations. Auditors look for existence and approval, but internal security teams rely on policies to define scope and boundaries.
Examples:
Access Control Policy – Defines user access principles, least privilege, and periodic reviews.
Incident Response Policy – Defines escalation criteria and response timelines.
Encryption Policy – States encryption standards for data at rest and in transit.
✅ Evidence: Dated, version-controlled, and management-approved copies of these documents.
2. Procedures & Playbooks
Step-by-step descriptions of how policies are enforced in practice.
Examples:
Onboarding & Offboarding Procedures – Detailed steps for granting/revoking access.
Change Management Procedures – Documented process for reviewing, approving, and testing production changes.
Incident Response Playbooks – Action plans for specific threats (e.g., phishing, ransomware).
✅ Evidence: Procedure documents, workflow diagrams, approval checklists.
3. System Logs & Screenshots
Technical evidence that shows the control is actually operating.
Examples:
IAM/SSO Logs – Show user access reviews, login history, and MFA enforcement.
Screenshots – MFA enabled on admin accounts, encryption configuration in AWS console.
Audit Trails – System-generated records of configuration changes, access approvals, or incident alerts.
✅ Evidence: Timestamped and stored in a secure repository.
4. Automation-Generated Evidence
Modern SaaS orgs thrive on automation — and automation produces consistent, trustworthy evidence.
Examples:
Jira / ServiceNow Tickets – Automatically generated for new user access requests or change approvals.
CI/CD Pipeline Logs – Records showing security tests run before deployment.
SIEM Alerts – Evidence of real-time monitoring and response to anomalies.
Vendor Risk Monitoring Tools – Continuous security ratings of third-party providers.
✅ Evidence: Raw log data, exportable reports, linked audit artifacts.
5. Independent Validation Evidence
Sometimes, auditors want assurance beyond internal controls. This comes from third-party testing.
Examples:
Vulnerability Scan Reports – Regular automated scans with remediation evidence.
Penetration Test Reports – Independent assessment of security posture.
External Audit or Certification Reports – Attestations from third parties on compliance status.
✅ Evidence: Reports stored securely with proof of management review.
Make Evidence Collection Part of the Control Lifecycle
Don’t wait until audit time to scramble for documents. Build evidence generation and storage into daily operations:
Automate where possible: Use GRC tools (Drata, Vanta, Tugboat Logic, Hyperproof, LogicGate) to pull evidence continuously.
Centralize evidence: Store artifacts in a secure, version-controlled repository (e.g., Confluence, SharePoint, GRC system).
Standardize formats: Use consistent templates for screenshots, logs, or tickets.
Schedule reviews: Conduct quarterly or semi-annual reviews to ensure evidence remains valid and relevant.
💡 Pro Tip: Define a “Control Evidence Checklist” for each control so team members know exactly what to capture and how often.
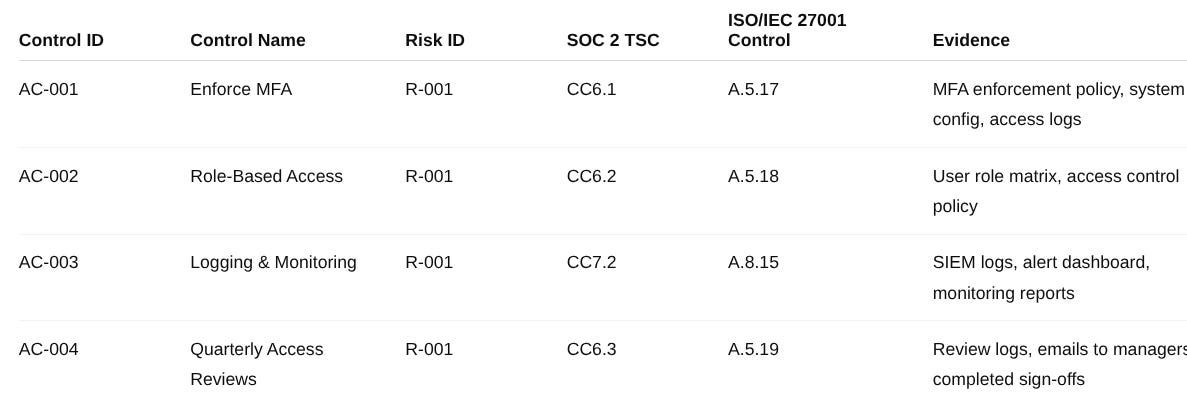
📊 Example: Evidence for an Access Control
This table makes it easy for auditors to validate that your control is real, operating, and consistent.
✅ Benefits of Strong Evidence
By building control evidence strategically, you achieve:
Audit readiness – Evidence is already packaged for SOC 2 / ISO 27001 audits.
Operational value – Security teams use the same evidence for incident response, monitoring, and reporting.
Efficiency – Automation reduces manual work and last-minute audit panic.
Assurance – Stakeholders and customers gain confidence in your program.
Evidence isn’t just an audit deliverable — it’s the proof of trustworthiness for your SaaS security program.
By embedding evidence generation into your daily processes and leveraging automation, you ensure that controls not only satisfy auditors but also make your organization measurably more secure.
Step 4: Integrate Framework Maintenance into Your GRC Program
Security and compliance are living processes, not projects you “finish.” For SaaS providers, where systems, data, and risks evolve constantly, a static compliance posture quickly becomes outdated — and dangerous.
To avoid “point-in-time” compliance that only works during the audit window, organizations must build continuous monitoring and governance cycles into their GRC program.
Why Framework Maintenance Matters
SOC 2 auditors (Type 2) want proof that controls operate consistently over months, not just at audit time.
ISO 27001 requires continual improvement — organizations must show evidence of monitoring, reviewing, and enhancing their ISMS.
Customers and regulators increasingly expect always-on assurance, not just annual certificates.
✅ A structured governance cycle ensures your GRC program is sustainable, repeatable, and resilient against new risks and compliance demands.
Building a Control Governance Cycle
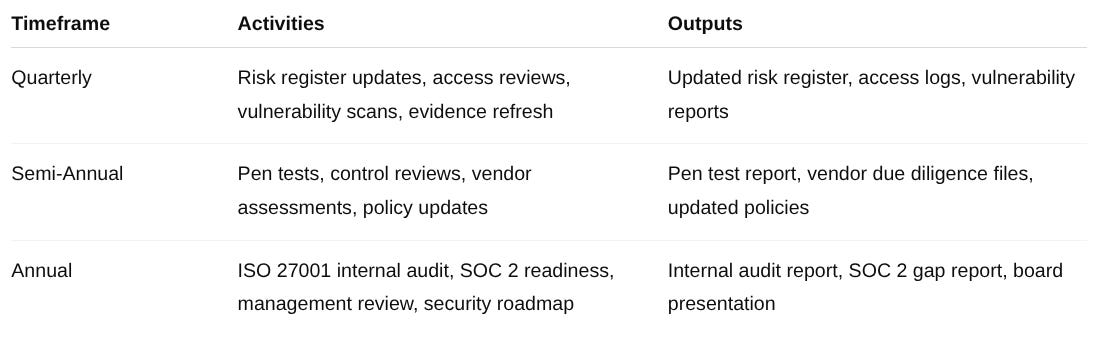
Here’s how SaaS organizations can structure their GRC program maintenance across quarterly, semi-annual, and annual cycles.
📅 Quarterly Activities – Keep Your Risk Posture Current
Review and Update Risk Register
Add new risks (e.g., from new SaaS features, cloud integrations, or regulatory changes).
Reassess likelihood and impact of existing risks.
Retire risks that are no longer relevant.
Conduct Access Reviews
Validate least privilege across critical systems (IAM, databases, admin panels).
Ensure terminated employees and contractors no longer have access.
Run Vulnerability Scans
Quarterly scans for infrastructure and SaaS applications.
Track remediation timelines and exceptions.
Update Control Evidence
Refresh audit artifacts (logs, tickets, screenshots).
Ensure evidence collection automation is functioning.
✅ Outcome: Risks stay up to date, and auditors can see ongoing risk management instead of “audit-season-only” activity.
📅 Semi-Annual Activities – Validate Control Effectiveness
Technical Control Testing
Perform penetration testing or red teaming to validate technical defenses.
Run phishing simulations or insider threat drills.
Control Effectiveness Reviews
Assess whether controls are mitigating risks as intended.
Adjust where gaps or inefficiencies are found.
Third-Party Vendor Reviews
Reassess critical vendors for compliance certifications and security posture.
Update vendor risk assessments in your GRC platform.
Policy and Procedure Updates
Revise documents to reflect organizational or regulatory changes.
Communicate updates to staff via security awareness refreshers.
✅ Outcome: Control environment is validated for effectiveness and adapted to evolving threats.
📅 Annual Activities – Align with Framework and Audit Requirements
ISO 27001 Internal Audit
Perform a complete internal audit of your ISMS.
Document nonconformities and corrective actions.
SOC 2 Readiness Assessment (if applicable)
Conduct a mock audit or gap assessment.
Validate readiness for the SOC 2 Type 1 or Type 2 report.
Management Review
Present risk posture, control effectiveness, and audit results to executive leadership.
Gain approval for risk acceptance decisions.
Strategic Roadmap Updates
Align security initiatives with business strategy.
Budget for tooling, staffing, or process improvements.
✅ Outcome: Your program remains aligned with compliance frameworks, leadership stays engaged, and auditors see evidence of continuous improvement.
How to Operationalize Framework Maintenance
GRC Platforms: Automate control monitoring and reminders (e.g., Hyperproof, LogicGate, Drata).
Dashboards & Metrics: Track KPIs (e.g., % of risks with treatment plans, time-to-remediate vulnerabilities).
Control Owners: Assign accountability — every control must have a responsible individual.
Audit Calendar: Maintain a calendar of evidence collection, reviews, and test dates.
Continuous Improvement Cycle (PDCA): Adopt ISO’s Plan-Do-Check-Act approach to ensure you’re not just maintaining but improving.
📊 Example: GRC Maintenance Calendar
Frameworks like SOC 2 and ISO 27001 aren’t check-the-box exercises — they’re designed to embed security as a continuous practice.
By building a governance cycle into your GRC program, your SaaS organization not only maintains compliance but also:
Improves resilience against evolving threats
Reduces audit fatigue through ongoing readiness
Gains executive buy-in with clear reporting cycles
Builds lasting trust with customers and stakeholders
Step 5: Design Policies that Reflect Both the Standard and Your Risk Profile
Policies are the foundation of your GRC program. They set the tone for security, define expectations, and provide auditors with the documented proof that your controls are intentional, consistent, and risk-driven.
But here’s the challenge: too many SaaS organizations write “checkbox policies” that auditors quickly see through.
“A one-liner policy like ‘We enforce MFA’ won’t hold up. Auditors, regulators, and your own teams expect policies that explain why the rule exists, how it’s enforced, and who is accountable.”
Done right, policies become more than documents — they are the connective tissue between your risks, controls, and compliance frameworks.
🎯 Why Policies Matter for SOC 2 and ISO 27001
SOC 2 auditors expect your policies to align with the Trust Services Criteria (TSC), demonstrate management oversight, and tie into your control activities.
ISO 27001 requires documented policies and procedures as part of the Information Security Management System (ISMS). Annex A controls (e.g., A.5.1: Policies for information security) make policies a non-negotiable.
Both frameworks want to see that policies are:
Reviewed and approved by management
Communicated to staff
Regularly updated to reflect changes in risk and operations
🧾 Anatomy of a Strong Policy
A well-crafted policy should answer five core questions:
Why? – What risk or business need does this policy address?
Example: “To mitigate the risk of unauthorized access to customer data…”
What? – What is the organization’s stance or requirement?
Example: “All production system access must be protected with MFA…”
Who? – Who owns, enforces, and follows the policy?
Example: “The IT Security Lead is responsible for implementation. All employees must comply.”
How? – What controls or procedures ensure compliance?
Example: “SSO integration with enforced MFA, quarterly access reviews…”
When? – What is the frequency of control activities and reviews?
Example: “MFA enforcement is continuous; policy reviewed annually.”
🧩 Linking Policies to Risk and Frameworks
Policies must be anchored to real risks and mapped to frameworks.
This makes them meaningful for both internal security and audit purposes.
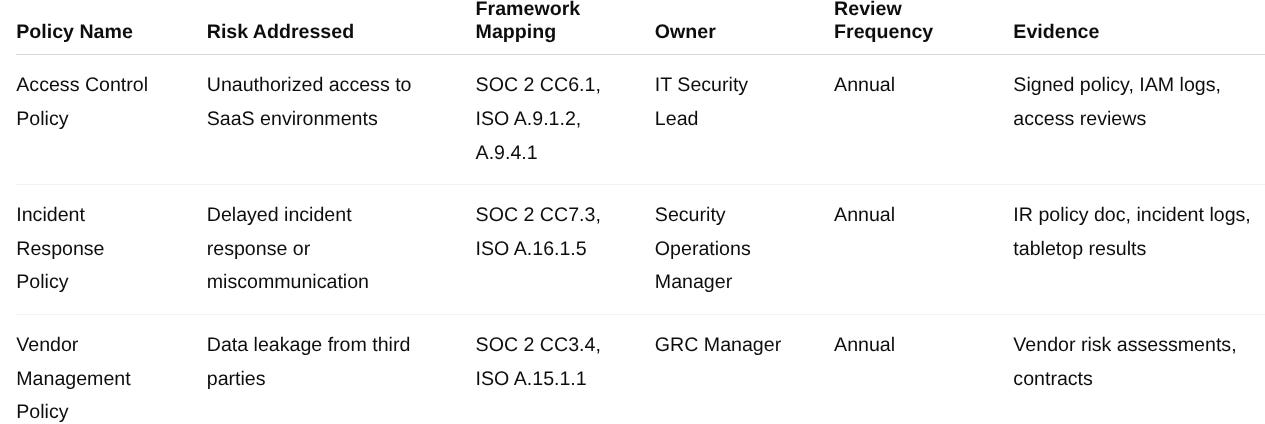
✅ Example: Access Control Policy
Rationale (Risk-Based): Risk of unauthorized access to customer data due to credential compromise.
Control Activities:
MFA required for all privileged accounts.
Role-Based Access Control (RBAC) enforced for least privilege.
Quarterly access reviews conducted by IT Security Lead.
Responsible Parties: IT Security Lead (owner), Department Heads (reviewers), All employees (users).
Frequency: MFA enforced continuously; access reviews quarterly; policy reviewed annually.
Framework Mapping:
SOC 2: CC6.1 – Logical access controls
ISO 27001: A.9.1.2 – User access provisioning; A.9.4.1 – Information access restriction
This single policy now:
Shows auditors how it addresses risks.
Provides operational guidance for staff.
Demonstrates framework alignment.
📂 Policy Categories That SaaS Organizations Must Cover
At minimum, SaaS providers aligning with SOC 2 and ISO 27001 should maintain policies in these areas:
Access Control Policy – Covers RBAC, MFA, and provisioning/de-provisioning.
Information Security Policy – High-level ISMS direction (ISO 27001 Clause 5.2).
Incident Response Policy – Outlines escalation, communication, and response procedures.
Change Management Policy – Defines how production changes are approved, tested, and rolled out.
Vendor Management Policy – Ensures third-party risk is assessed and monitored.
Encryption & Data Protection Policy – Specifies encryption requirements and key management.
Acceptable Use Policy (AUP) – Governs employee use of IT assets.
Business Continuity & Disaster Recovery Policy – Aligns with resilience objectives.
Vulnerability & Patch Management Policy – Defines timelines for remediation.
Training & Awareness Policy – Ensures staff are trained on security responsibilities.
📌 ISO 27001 (Annex A) gives a detailed control reference; SOC 2 auditors will test whether these policies are enforced consistently.
🔄 Maintaining Policies Over Time
Policies are not “set and forget.” To keep them effective:
Review Annually: At minimum, review policies once per year and after major business or risk changes.
Version Control: Use a system (e.g., Confluence, SharePoint, Git-based repos) to track versions, changes, and approvals.
Executive Approval: All policy updates should be signed off by leadership (CEO, CISO, or equivalent).
Staff Acknowledgment: Employees should attest annually that they’ve read and understood policies.
Audit Trail: Maintain logs of reviews, approvals, and employee acknowledgments for auditors.
📊 Example: Policy Design Table
Policies are more than paperwork — they are the governance backbone of your SaaS security program.
By designing policies that:
Link to risks (why they exist)
Define control activities (how they’re enforced)
Assign ownership and frequency (who and when)
…you create a policy framework that is not only audit-ready, but also operationally valuable.
This approach ensures your policies evolve alongside your risks, business, and compliance obligations.
Common Control Areas to Focus On (with Risk and Framework Alignment)
Every SaaS company has unique risks, but certain control areas are universal.
They form the core of both SOC 2 and ISO 27001, and they address the most common threats to cloud-native businesses: unauthorized access, weak vendor oversight, unmonitored incidents, and delayed recovery.
Here’s a breakdown of key control domains, the business risks they mitigate, and their framework mappings.
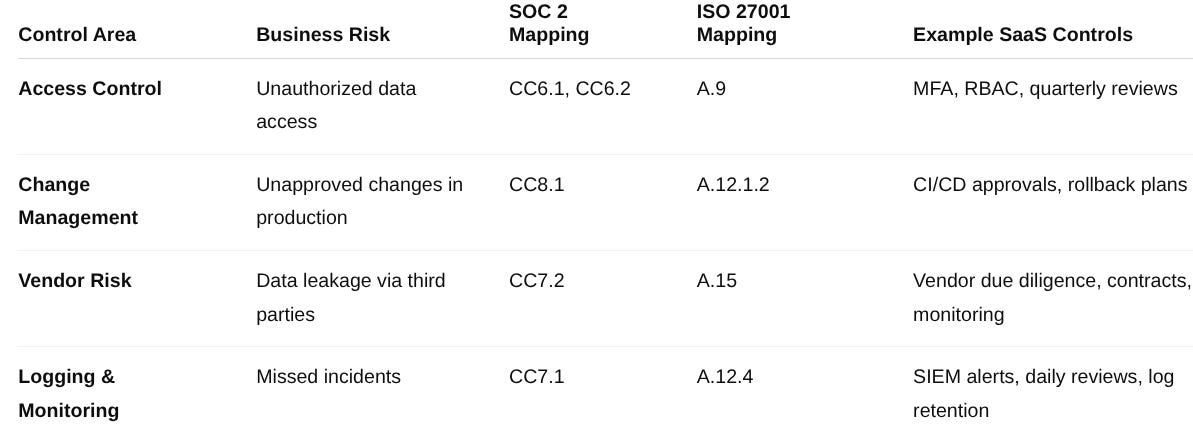
🔑 1. Access Control
Business Risk: Unauthorized access to customer data or production systems due to credential theft, privilege creep, or poor offboarding practices.
SOC 2 Mapping: CC6.1 (Logical access controls), CC6.2 (Role-based access).
ISO 27001 Mapping: A.9 (Access Control).
Typical SaaS Controls:
Single Sign-On (SSO) with MFA for all critical systems.
Role-Based Access Control (RBAC) and least privilege.
Automated provisioning/de-provisioning tied to HR systems.
Quarterly access reviews documented in Jira or GRC tools.
✅ Auditor Tip: Evidence must include policies, IAM logs, and completed access review records.
⚙️ 2. Change Management
Business Risk: Unauthorized or untested code changes in production could cause downtime, data integrity issues, or security vulnerabilities.
SOC 2 Mapping: CC8.1 (Change management).
ISO 27001 Mapping: A.12.1.2 (Change management).
Typical SaaS Controls:
CI/CD pipelines enforce peer review and security testing.
Separation of duties between developers and deployers.
Change approvals tracked in Jira/ServiceNow.
Rollback plans for critical updates.
✅ Auditor Tip: Provide change request tickets, approval logs, and evidence of testing before deployment.
🌐 3. Vendor Risk Management
Business Risk: Data leakage or service disruption caused by third-party SaaS providers, cloud vendors, or contractors.
SOC 2 Mapping: CC7.2 (Vendor and subservice provider risk).
ISO 27001 Mapping: A.15 (Supplier relationships).
Typical SaaS Controls:
Vendor onboarding questionnaires and security reviews.
Contracts requiring SOC 2 / ISO 27001 certifications.
Continuous vendor monitoring tools (e.g., SecurityScorecard, UpGuard).
Annual reassessment of critical vendors.
✅ Auditor Tip: Maintain a vendor risk register with evidence of due diligence and monitoring.
📊 4. Logging & Monitoring
Business Risk: Missed security incidents or delayed detection due to lack of visibility into systems and applications.
SOC 2 Mapping: CC7.1 (Monitoring activities).
ISO 27001 Mapping: A.12.4 (Logging and monitoring).
Typical SaaS Controls:
Centralized log management (SIEM).
Alerts for anomalous activity (failed logins, privilege escalation).
Daily log reviews by SOC or automated tools.
Retention policies aligned with legal/regulatory needs.
✅ Auditor Tip: Show sample alerts, SOC investigation notes, and retention configurations.
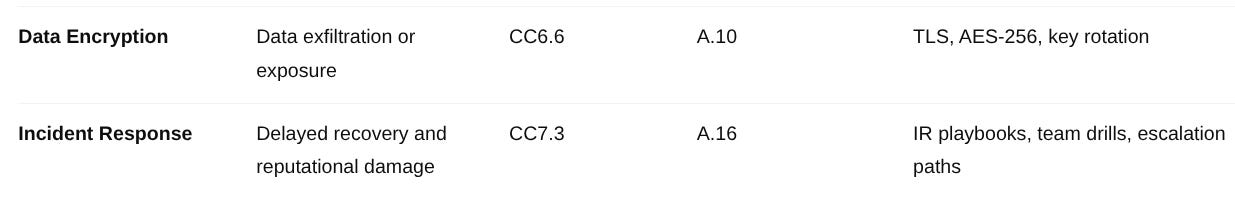
🔒 5. Data Encryption
Business Risk: Data exfiltration or exposure due to unencrypted storage or weak encryption in transit.
SOC 2 Mapping: CC6.6 (Encryption and key management).
ISO 27001 Mapping: A.10 (Cryptography).
Typical SaaS Controls:
TLS 1.2+ enforced for all network traffic.
AES-256 encryption at rest in databases and object stores.
Key management via AWS KMS or HashiCorp Vault.
Regular rotation of encryption keys.
✅ Auditor Tip: Provide encryption configs, screenshots, and key rotation logs.
🚨 6. Incident Response
Business Risk: Prolonged downtime or reputational damage due to slow detection and response to incidents.
SOC 2 Mapping: CC7.3 (Incident response).
ISO 27001 Mapping: A.16 (Information security incident management).
Typical SaaS Controls:
Documented IR policy and playbooks.
Defined incident severity levels and escalation procedures.
Incident Response Team (IRT) with assigned roles.
Tabletop exercises conducted annually.
✅ Auditor Tip: Keep IR policy docs, incident logs, and tabletop exercise reports ready.
📋 Expanded Control Area Table
Focusing on these six common control areas ensures your SaaS organization addresses both high-impact risks and core compliance requirements.
By mapping each control to both SOC 2 and ISO 27001, you create a single security language that:
Reduces duplication of effort.
Demonstrates audit readiness.
Ensures operational effectiveness.
Think of this table as the minimum control baseline every SaaS provider should implement and maintain.
Final Thoughts: Think Holistically, Document Strategically
Risk-based controls and framework alignment aren’t competing priorities—they’re complementary pillars of a modern SaaS security strategy. SOC 2 and ISO 27001 provide the scaffolding, but your risk program supplies the substance. When mapped together, they transform compliance from a once-a-year exercise into an engine of continuous assurance.
The takeaway is simple: controls should never be implemented for the audit alone. They should exist because they defend the business, and the audit should simply confirm what’s already true — that your security program is consistent, risk-driven, and trustworthy.
By documenting the link from risk → control → framework → evidence, SaaS companies can deliver both operational protection and audit success. A certificate proves you can pass an audit. A resilient program proves you can protect customers, adapt to new risks, and maintain trust over time. SaaS companies that link risk → control → framework → evidence aren’t just audit-ready — they’re market-ready.
📚 References
AICPA – SOC 2®: Trust Services Criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy (2022)
https://us.aicpa.org/soc4soISO/IEC 27001:2022 – Information Security, Cybersecurity and Privacy Protection — Information Security Management Systems — Requirements
https://www.iso.org/standard/82875.htmlISO/IEC 27005:2022 – Information Security, Cybersecurity and Privacy Protection — Guidance on Information Security Risk Management
https://www.iso.org/standard/80585.htmlNIST SP 800-37 Rev. 2 – Risk Management Framework for Information Systems and Organizations (2018)
https://csrc.nist.gov/publications/detail/sp/800-37/rev-2/finalNIST SP 800-30 Rev. 1 – Guide for Conducting Risk Assessments (2012)
https://csrc.nist.gov/publications/detail/sp/800-30/rev-1/finalOWASP Top Ten Project – Common Web Application Security Risks (2021)
https://owasp.org/www-project-top-ten/MITRE ATT&CK Framework – Adversary Tactics, Techniques, and Common Knowledge https://attack.mitre.org